Phishing Attacks in Crypto: How Scammers Steal Your Keys and How to Stop Them
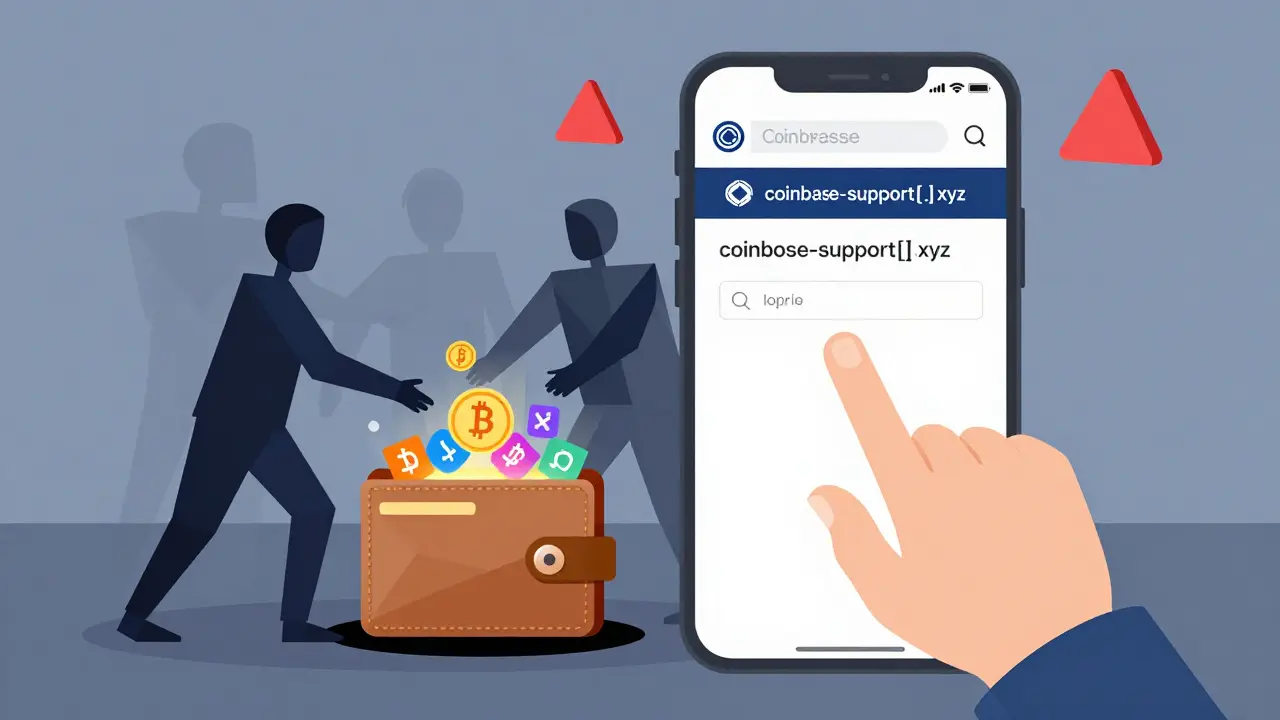
When you hear phishing attacks, deceptive attempts to steal your crypto by pretending to be a trusted service, think of a fake email that looks like Binance, a fake website that copies MetaMask, or a DM from someone claiming to be support. These aren’t just annoying—they’re how people lose everything in seconds. BIP39 seed phrases, the 12-24 word backup that controls your entire wallet are the ultimate target. Once a scammer gets that, they don’t need your password, your email, or your phone—they own your coins. And there’s no reset button.
Most fake websites, cloned pages designed to trick you into entering your seed phrase or signing a malicious transaction look perfect. They copy logos, colors, even the URL structure. But they’re not hosted by the real company—they’re on random domains like metamask-support[.]xyz or binance-verify[.]live. You won’t see the warning until it’s too late. And it’s not just about logging in. Some phishing scams trick you into signing a transaction that lets them drain your wallet the moment you click "Approve". That’s why wallet security, the practice of never sharing your seed phrase and double-checking every transaction isn’t optional—it’s your last line of defense. Even if you’re careful, scammers use urgency: "Your wallet will be locked in 5 minutes!" or "Claim your airdrop before it expires!"—both lies. The real exchanges don’t DM you. The real airdrops don’t ask for your seed phrase.
Look at the posts below. You’ll see real cases: the HAI token scam that used fake airdrop claims to steal funds, the Unnamed.Exchange review that warned about anonymous platforms with no trust signals, and the NAMA Protocol mix-up where people got tricked into thinking a non-existent airdrop was real. These aren’t edge cases—they’re the playbook. Every single one of these scams relies on the same trick: making you act before you think. You don’t need to be a tech expert to stay safe. You just need to pause. Never click a link from a DM. Always type the URL yourself. Never sign anything you don’t fully understand. And if something feels off? It probably is. The next time you see a "free token" offer or a "security update" pop-up, remember: if it’s too good to be true, or too urgent to ignore, it’s a phishing attack waiting to happen.
Cryptocurrency Phishing Scams Explained: How They Work and How to Stop Them
Cryptocurrency phishing scams trick users into giving up private keys or sending crypto to fake sites. Learn how they work, the most common types, and how to protect yourself from losing your digital assets forever.
learn more